Security Insights: Cybersecurity for Remote Teams – Must-Have Practices
Introduction
Remote work is no longer a temporary shift — it’s the new normal.
But with flexibility comes a new set of security challenges.
Every unsecured Wi-Fi network, personal laptop, and shared document link can open a door to potential threats.
In today’s distributed world, cybersecurity isn’t just an IT issue — it’s a team discipline.
Let’s look at the essential practices every remote-first organization should follow to keep data, systems, and employees safe.
1. Start with Zero Trust
The traditional perimeter security model (“inside = safe, outside = unsafe”) no longer works.
Instead, Zero Trust assumes no device or user should be trusted by default.
Core Principles:
- Verify identity continuously (MFA, SSO)
- Enforce least-privilege access
- Monitor all activity with behavioral analytics
- Encrypt every communication channel
Adopt the mindset: “Never trust, always verify.”
2. Use Strong Identity and Access Management (IAM)
Identity is the new security boundary.
Cloud apps, SaaS tools, and shared credentials all create weak points if not properly managed.
Best Practices:
- Implement Single Sign-On (SSO) for unified control
- Enforce Multi-Factor Authentication (MFA) everywhere
- Regularly audit user permissions
- Revoke access immediately when roles change
Tools to explore: Okta, AWS IAM, Microsoft Entra, Google Workspace Admin.
3. Secure Endpoints (Laptops, Phones, Tablets)
Every device that connects to your network is a potential attack surface.
Endpoint protection ensures threats don’t slip through remote access channels.
What to Implement:
- Mandatory antivirus and EDR (Endpoint Detection & Response)
- OS and patch updates automated
- Full-disk encryption (BitLocker, FileVault)
- Remote wipe capabilities for lost devices
4. Use VPNs or Zero-Trust Network Access (ZTNA)
Public Wi-Fi is a hacker’s playground.
Always route traffic through encrypted tunnels using VPNs or, better yet, ZTNA frameworks.
Difference:
- VPN: Encrypts traffic but still trusts the network once connected.
- ZTNA: Verifies identity for every single connection.
ZTNA is the modern replacement for traditional VPNs — faster, safer, and identity-centric.
5. Protect Collaboration Tools
Slack, Zoom, Google Drive, Notion — these tools make remote work possible but also expose sensitive data.
Recommendations:
- Restrict file sharing to company domains
- Enable content scanning and DLP (Data Loss Prevention)
- Require strong meeting passwords
- Review integrations and third-party bots
Security must extend to where people actually work — the apps themselves.
6. Email and Phishing Awareness
Even the best firewalls can’t stop a clever phishing email.
Human error remains the top cause of breaches.
Practical Steps:
- Regular phishing simulations
- Training on recognizing malicious links
- Using email filtering (Microsoft Defender, Proofpoint)
- Reporting suspicious activity immediately
Encourage a no-blame culture — better to report false alarms than miss real threats.
7. Data Encryption and Backups
Data loss can come from attacks or accidents.
Encryption ensures stolen data is useless; backups ensure it’s recoverable.
Checklist:
- Encrypt data at rest and in transit
- Maintain off-site backups or use cloud redundancy
- Test restoration procedures quarterly
- Use services like AWS KMS, Google Cloud KMS for key management
8. Security Policies and Culture
Cybersecurity tools are only as strong as the habits behind them.
Build a security-first culture by setting clear expectations:
- Mandatory password rotation and MFA
- Remote work security policy (devices, Wi-Fi, data handling)
- Incident response checklist
- Regular team refreshers and tabletop exercises
Security is everyone’s responsibility — not just the IT department’s.
Simple Flow Diagram
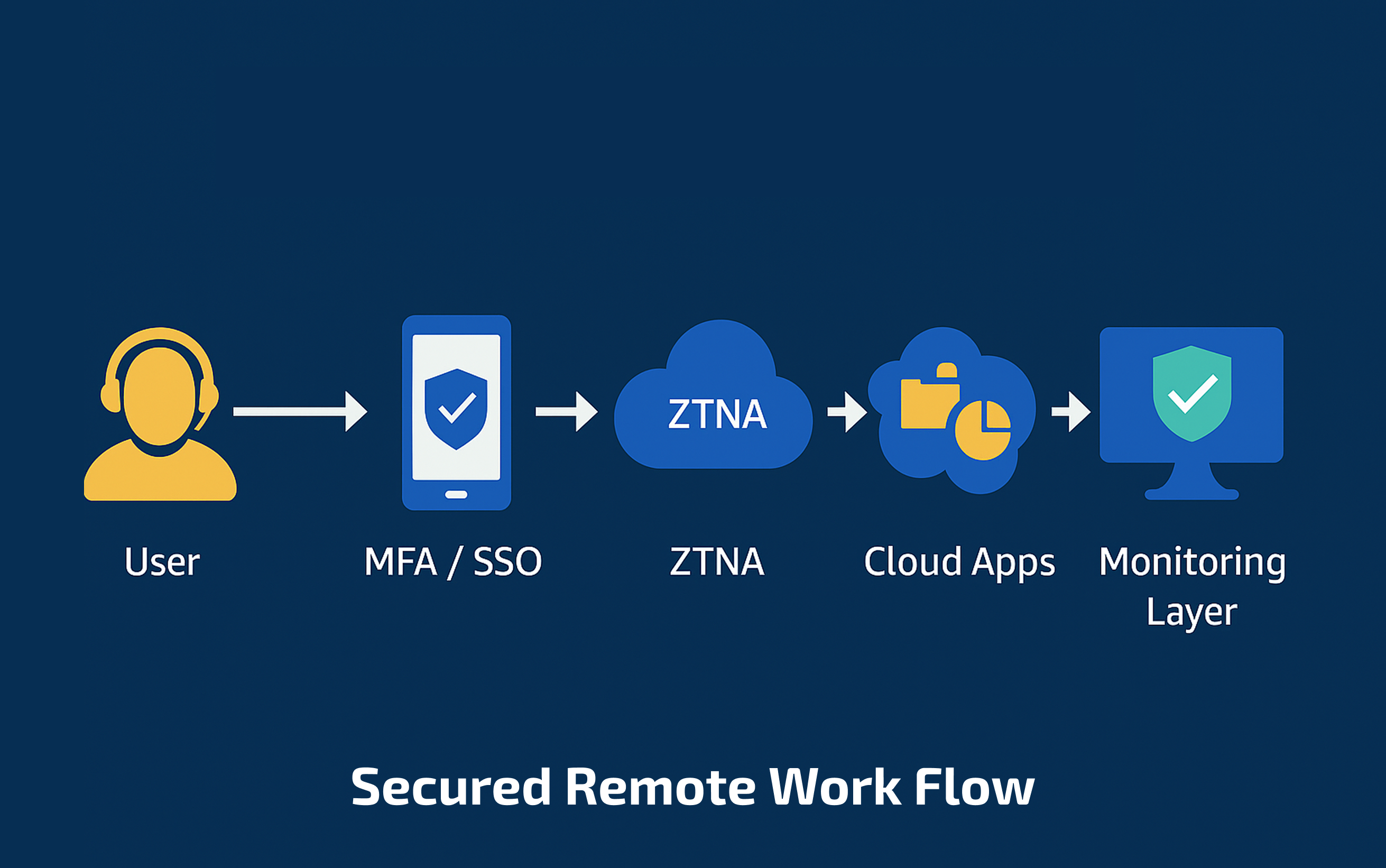
Figure: Secure Remote Work Architecture – User to Cloud, Safely
Conclusion
Remote work has blurred the boundaries of traditional corporate security.
Your team’s living room is now part of your network, and every connected device is a new door to protect.
By enforcing Zero Trust, securing endpoints, and building a proactive security culture, companies can enjoy the flexibility of remote work without compromising safety.





No comments yet. Be the first to comment!