AWS: Security in a Multi-Cloud Environment
Introduction:
Multi-cloud is no longer a theoretical architecture choice. Many teams arrive at it gradually — through acquisitions, vendor requirements, regional constraints, or the need to avoid deep lock-in. Over time, AWS starts sharing responsibility with other cloud platforms, and security becomes one of the first areas where cracks appear.
The challenge with multi-cloud security is not that any single cloud is insecure. It’s that security models, assumptions, and tooling differ subtly across providers. Without a clear strategy, teams end up with fragmented controls, inconsistent visibility, and unclear ownership.
This blog looks at how to think about security in a multi-cloud environment with AWS as the anchor, focusing on principles that scale rather than provider-specific tricks.
The Real Security Challenge in Multi-Cloud:
The biggest misconception about multi-cloud security is that it’s about configuring multiple platforms correctly. In reality, the harder problem is consistency.
Each cloud provider has its own:
- identity model
- networking abstractions
- logging formats
- security tooling
When teams treat each cloud in isolation, security posture becomes uneven. One environment is tightly controlled, while another quietly drifts. Attackers exploit gaps, not platforms.
The goal in multi-cloud security is not uniform tooling, but uniform intent.
Diagram: AWS Shared Responsibility Model in a Multi-Cloud Context
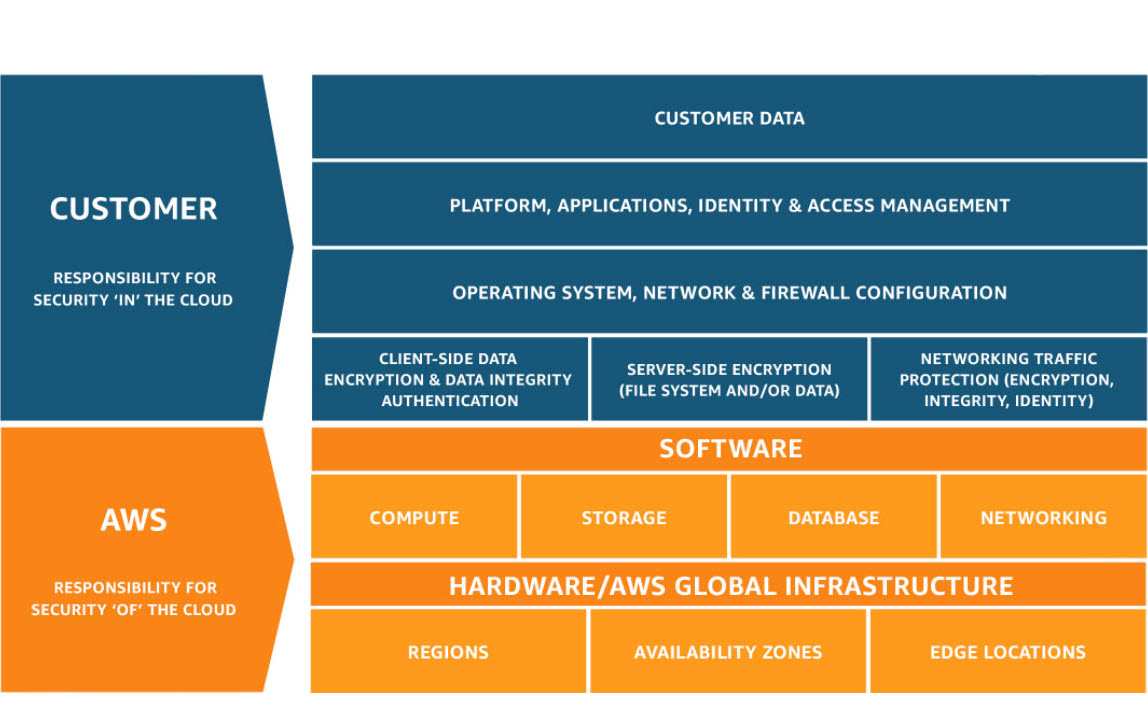
Figure: Illustration of AWS’s shared responsibility model, highlighting how security ownership is divided between AWS and customers — a key consideration when extending security practices across multiple cloud providers. Source: Shared Responsibility Model
Identity Should Be Centralised, Not Duplicated:
Identity is the foundation of cloud security, and multi-cloud setups often weaken it unintentionally. Creating separate IAM systems per cloud leads to sprawl, over-privileged access, and audit complexity.
A more resilient approach is to centralise identity and let clouds consume it. AWS IAM integrates well with external identity providers, allowing organisations to enforce consistent authentication and authorization rules across environments.
Practically, this means:
- a single source of truth for users and roles
- short-lived credentials instead of static keys
- clear separation between human and service identities
When identity is centralised, access reviews and incident response become significantly easier.
Network Security Must Assume Inter-Cloud Exposure:
In single-cloud architectures, teams often rely heavily on network isolation as a security boundary. Multi-cloud architectures challenge that assumption.
Inter-cloud connectivity — whether through VPNs, private links, or public endpoints — increases the attack surface. Treating traffic between clouds as “trusted” is risky.
A safer approach is to:
- treat inter-cloud traffic as untrusted by default
- apply encryption everywhere, not just at the perimeter
- enforce explicit allow-lists between services
Zero-trust principles become far more relevant once workloads span providers.
Logging and Visibility Are Where Most Teams Struggle:
Security without visibility is guesswork. In multi-cloud environments, logs often live in separate systems, making correlation slow and incomplete.
AWS provides rich logging through services like CloudTrail, VPC Flow Logs, and GuardDuty. The challenge is ensuring logs from other clouds reach a central analysis point.
Teams that succeed here usually:
- standardise log formats where possible
- forward logs to a central SIEM or data lake
- define consistent alerting rules across clouds
The objective is not identical logs, but comparable signals that allow teams to detect anomalies quickly.
Shared Responsibility Becomes Harder to Communicate:
Cloud providers operate under a shared responsibility model, but that model becomes harder to explain and enforce in multi-cloud setups.
Different teams often assume different boundaries of responsibility depending on the provider. Over time, this leads to gaps — especially around patching, configuration management, and monitoring.
Clear documentation and ownership are essential. Teams should be explicit about:
- what AWS secures by default
- what the organisation must secure
- how those responsibilities differ across clouds
Ambiguity is one of the biggest security risks in multi-cloud environments.
Tooling Strategy Matters More Than Tool Count:
It’s tempting to adopt cloud-native security tools from every provider. While these tools are powerful, using all of them independently often overwhelms teams.
A more sustainable approach is to:
- use cloud-native tools for deep, provider-specific visibility
- complement them with cross-cloud tooling for governance and reporting
- avoid duplicating controls unnecessarily
AWS security services can act as a strong baseline, but they work best when integrated into a broader security strategy rather than operating in isolation.
Incident Response Must Be Cloud-Agnostic:
When incidents occur, teams don’t have time to remember which cloud behaves differently. Response processes must be consistent, even if underlying tools differ.
Effective multi-cloud incident response relies on:
- predefined playbooks that work across providers
- centralised logging and alerting
- clear escalation paths and ownership
Practicing incident response in a multi-cloud context is just as important as designing it.
Conclusion:
Security in a multi-cloud environment is not about mastering every provider’s feature set. It’s about maintaining clarity as complexity grows.
AWS remains a strong foundation for security, but its effectiveness in multi-cloud architectures depends on how well teams centralise identity, enforce consistent controls, and maintain visibility across environments.
Teams that approach multi-cloud security deliberately — with shared principles and clear ownership — can scale safely. Those who treat it as a collection of independent setups often discover weaknesses only after something goes wrong.





No comments yet. Be the first to comment!